Installing SSH server on Windows 10
Microsoft natively supports SSH client and SSH server via libreSSH, but has some caveats, at least on Windows 10. According to the official docs it should be installable via the Features interface, but this was not quite so in my experience.
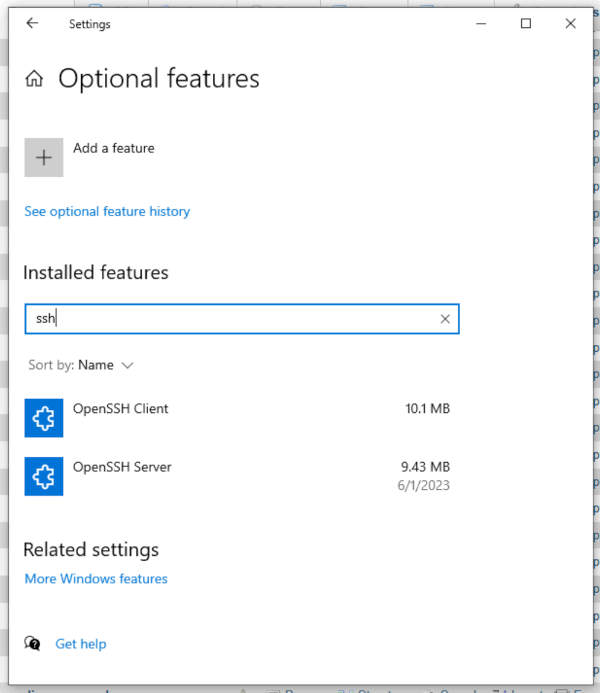
The official instructions list that it should be installable simply by browsing to Settings -> Apps -> Optional Features, and selecting to install "OpenSSH Server". As with most things Microsoft, (or so I've personally found), it just doesn't work.
I saw "OpenSSH Client" in the list, but the server was no where to be found. As such, I had to resort to the command line to install it instead, (so much for Windows being a GUI-friendly OS, eh?).
Installing SSHD
To run it, this needs to be installed as sudo. Unfortunately this OS does not ship with any sudo functionality, so instead search for "Powershell" in the start menu, right click on the application shortcut, and select "Run as Administrator".
Add-WindowsCapability -Online -Name OpenSSH.Server~~~~0.0.1.0
Once this powershell command was ran from an elevated privilege terminal, "OpenSSH Server" was displayed in the Optional Features interface, as listed above.
A configuration tweak is needed in ProgramData/ssh/sshd_config, but the service needs to be started before this directory is populated.
From the same administrator-level powershell window, start the service to create these files.
Start-Service sshd
Set-Service -Name sshd -StartupType 'Automatic'
Configuring with Sane Defaults
Then, sudo edit the sshd_config file, (again with the same Start -> Notepad -> right click, "Run as Administrator") and open the file, (while selecting "All Files" to show).
Comment out the lines at the bottom listed as "Match Group administrators AuthorizedKeysFile...". This will force all users with admin permission to use the programdata as their source directory.
This defeats the purpose of having different user accounts, is just weird, and doesn't seem to work anyway.
I also recommend uncommenting "# PasswordAuthentication yes" and change it to "no". This will disable password auth, (as SSH should ALWAYS use keys for every user).
Once saved, restart the service, add your public key to ~/.ssh/authorized_keys, and test it out.
Restart-Service sshd
Issues and Debugging
When you encounter issues, you can enable verbose logging by setting the following lines:
# Logging
SyslogFacility LOCAL0
LogLevel Debug3
Restart the service and a log file should be created in ProgramData/ssh/logs/sshd.log.
One issue I encountered was "get_passwd: Invalid account type 3.". According to bug reports this appears to be caused by the user name being the same name as the hostname, and the Win32 API doesn't understand that user authentication was requesting a user as opposed to the host.